Part 3 of this article series focuses on the market for cloud-based IGA solutions (Identity Governance & Administration) — the new buzzword for managing identities and authorizations (IAM).
This market is so densely populated that a complete evaluation of all available options is practically impossible. There are highly specialized analysts such as KuppingerCole and Gartner who can undoubtedly provide more comprehensive and detailed assessments of the IAM solutions landscape.
However, our perspective in this series is different.
We are addressing SAP IDM customers specifically and presenting possible alternatives that we, as an independent service provider with decades of experience in SAP customer projects, consider relevant.
In practice, all cloud services share the same fundamental issue:
They are no longer, as with SAP IDM, highly flexible custom software, but standardized software that is usually only slightly or not at all customizable. Therefore, booking or implementing a cloud service must always be preceded by a thorough check for potential showstoppers.
If no showstoppers exist — or if your company is flexible enough to respond through process standardization (see also Part 1 of this series) — cloud services offer benefits that cannot be ignored.
You’ve surely heard the sales slogan: “You focus on your business, and we take care of the rest.”
With streamlined processes and the right cloud services, this can actually become reality.
Please note that these assessments are not final and do not replace individual consulting.
Overview of the Series
- Part 1: The End of an Era – The Future After SAP IDM
- Part 2: SAP – Cloud Identity Services, GRC edition for SAP HANA
- Part 3: Cloud Services
- Part 4: On-Premise Solutions (e.g. One Identity)
Options Presented in This Article
- Option A: Microsoft Entra
- Option B: Omada Identity Cloud
- Option C: Okta
- Option D: IBM Security Verify
Option A: Microsoft Entra
The DSAG Technology Days 2024 in Hamburg had just kicked off on February 6, when Jürgen Müller (CTO SAP)and Sebastian Westphal (DSAG Board Member) made what is likely the most important announcement of the yearin the field of Identity and Access Management.
What had long been known to insiders and heavily speculated in the rumor mill was confirmed with a single slide — declaring Microsoft Entra as the “official successor” to SAP IDM.
But what exactly is Microsoft Entra?
Formerly known as Azure Active Directory (Azure AD), Entra ID is a cloud-based identity and access management solution.
It provides authentication and authorization services for various Microsoft offerings such as Microsoft 365, Dynamics 365, and Microsoft Azure.
On July 11, 2023, Microsoft announced the renaming of Azure AD to Microsoft Entra ID to ensure consistent branding across its cloud portfolio.
The on-premise predecessor of Entra is the well-known Microsoft Active Directory (AD) — a directory service introduced in 1999, which has since become the de facto standard for managing Windows user accounts, application permissions, and email accounts.
Due to the quasi-monopolistic position of Microsoft products in the business world, Active Directory is used by virtually all SAP customers in one form or another.
In many organizations, all identities, the organizational structure, and access information for numerous applications reside within the AD structure.
For this reason, in many SAP IDM implementations, the first non-SAP system integrated into the IAM infrastructure as an identity provider and/or target system is Active Directory itself.
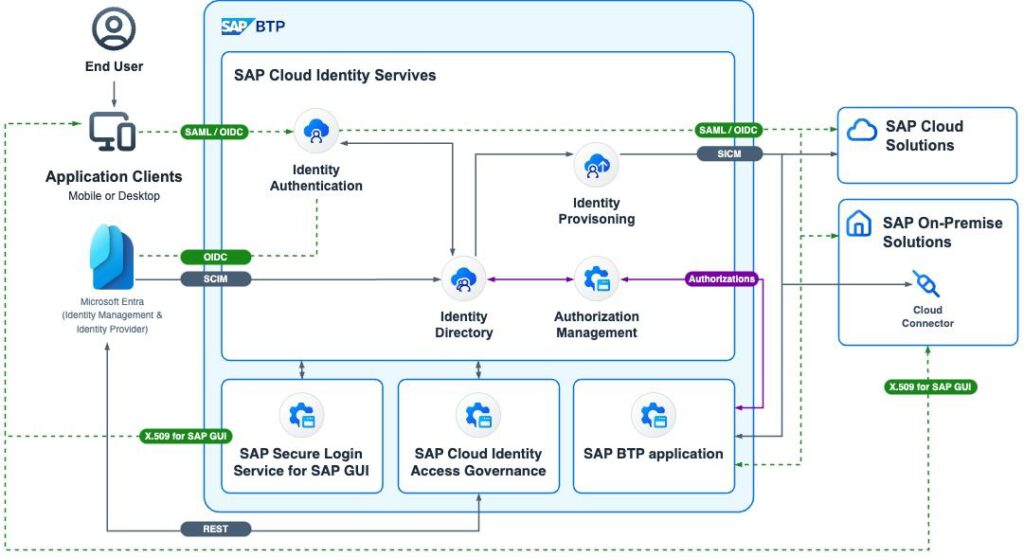
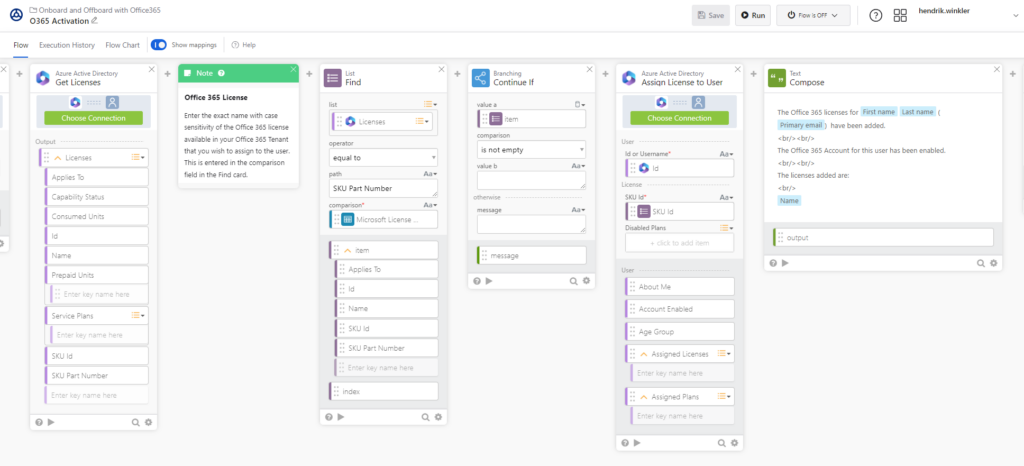
Following the DSAG announcement, SAP published a blog post presenting an architecture that will most likely serve as the reference model for the coming years. The diagram shows Entra as the central identity provider and identity management solution, integrated via interfaces with the SAP Cloud Identity Services and Cloud IAG. The Identity Provisioning Service (IPS), connected through the Cloud Connector, is responsible for bridging the gap between cloud and on-premise solutions. Although this architecture may appear complex at first glance, it offers a major advantage:
SAP-centric organizations already have Entra (formerly Azure AD), SAP IAS, and IPS in use within their cloud environments.
If you or your company work with Office 365 and/or Azure applications, it is highly likely that you already have your own instance of Entra in operation.
Upon login, Entra welcomes the user or administrator with a clean and organized interface.
Even a quick look at the menu reveals, to the trained eye, the general scope of the application:
- Users and Groups – Directory service (as known from Active Directory)
- Applications and Devices – Connectors / configuration management
- Protection – Authentication, password management
- External Identities – Collaboration with identities outside the organization
- Governance – Identity lifecycle, privileged access management (PAM)
For provisioning to external systems, the Azure AD Provisioning Service is used, which provides access to a range of applications.
SAP connectors can also be configured—albeit with some effort.
Provisioning is implemented via the SCIM protocol, which, to our knowledge, offers few options beyond standard functionality.
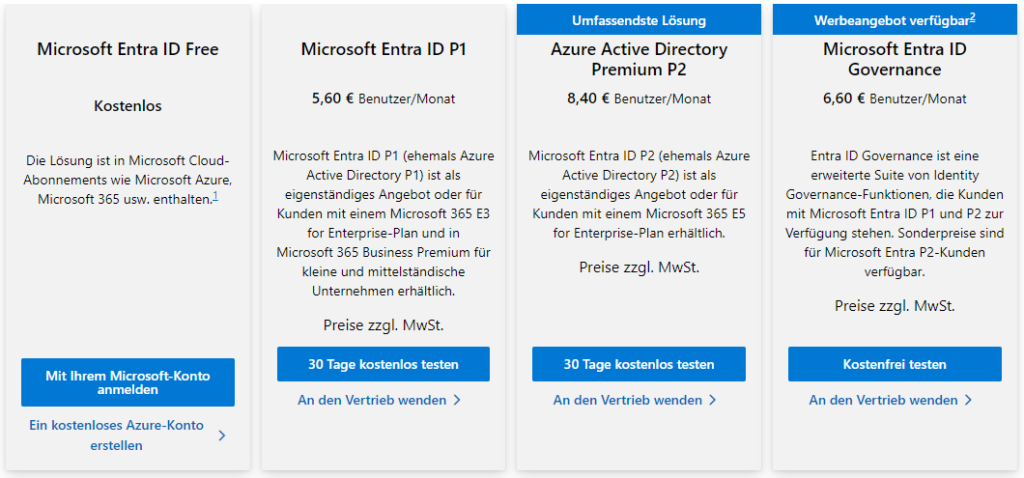
Another positive aspect of Entra is its pricing transparency. While SAP customers often have little clarity about what they actually pay for their applications, Entra stands out with a pricing model so simple it could practically fit on a beer coaster. However, it should be noted that the designated infrastructure involving SAP would, of course, also include costs for the respective SAP products.
Advantages
- Service is usually already available, even independently of the IAM architecture
- Slim architecture without additional third-party systems
- Partnership with SAP
- Modern application
- Excellent documentation
Disadvantages
- Additional lock-in effect toward Microsoft products
- Customers are inevitably exposed to subscription price increases
- No support for distributed domains
- On-premise infrastructure (e.g., Windows domain controllers) still requires the classic Active Directory
- The extent of SAP’s partnership, and thus the level of support and adaptability for extended SAP integration scenarios, remains to be seen
Assessment
Quiz question: What is Entra’s unbeatable advantage? Network effects!
Microsoft’s quasi-monopoly on business application software is not only a sound investment tip on the stock market but also a valid strategic argument when planning your next IAM landscape.
As with other cloud solutions, however, the Achilles’ heel—despite SAP partnership—will likely remain limited flexibility regarding customer-specific requirements.
Whether the standard infrastructure, consisting of Entra, IAS/IPS, and IAG, will ever be able to provision custom ABAP tables and fields, remains doubtful.
We are open to being positively surprised!
Option B: Omada Identity Cloud
All under one roof!
The Omada Identity Cloud is the modernized cloud edition of the Omada Identity Manager.
It provides all essential capabilities for the secure, compliant, and efficient management of user access to systems, data, and applications across hybrid, cloud, and multi-cloud environments.
Built on a modern, cloud-native microservices architecture, Omada delivers speed, intelligent decision support, connectivity, and higher performance than its predecessor products.
The solution itself is based on more than 20 years of experience and focuses on providing fast and reliable results for enterprises.
Conceptually, it includes:
- the best-practice framework for identity governance processes (IdentityPROCESS+)
- a deployment and operational methodology (IdentityPROJECT+)
- and guaranteed customer value through training, support, and professional services (Identity Success)
Integration capabilities are excellently documented in the Omada Connectivity Library.
With no other product is it easier for us to evaluate an existing infrastructure’s compatibility with the connectors of the IAM solution.

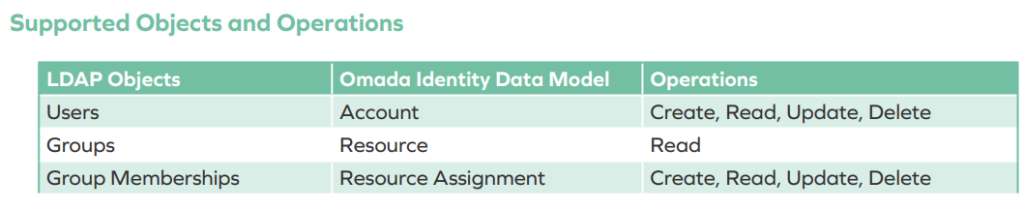
In the case of a planned SAP integration, we were able to find all commonly used connectors already available.
The supported objects and operations are listed for each connector.
The Omada team has indicated that, upon request, custom “special requirements” can also be implemented if the standard scope does not fully meet a customer’s needs.
Also worth highlighting is the strongly promoted promise of a fast and efficient implementation.
Through the Accelerator Package, Omada offers a standardized project and implementation methodology for deploying the software and its processes.
A project duration of 12+ months, which is typically expected (and also recommended by us) for an IAM implementation, is claimed to be reducible to just 4 weeks in many cases — a process only possible with a highly standardized and fully developed software solution.
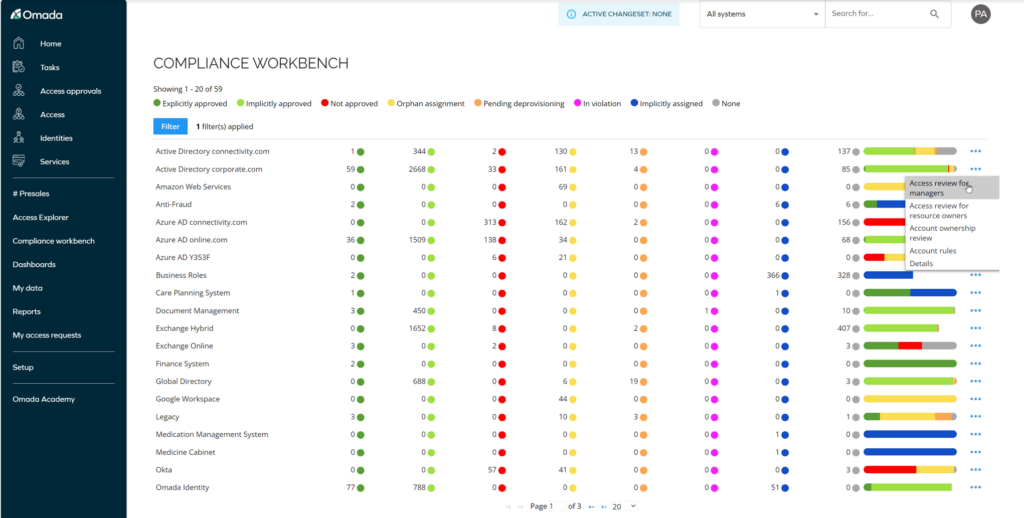
To illustrate this point, the Compliance Workbench and the Access Review feature will be shown as examples.
The Compliance Workbench provides a standardized overview of all integrated systems and evaluates assignments based on their current status — a simple way to identify major gaps in processes across the entire system landscape.
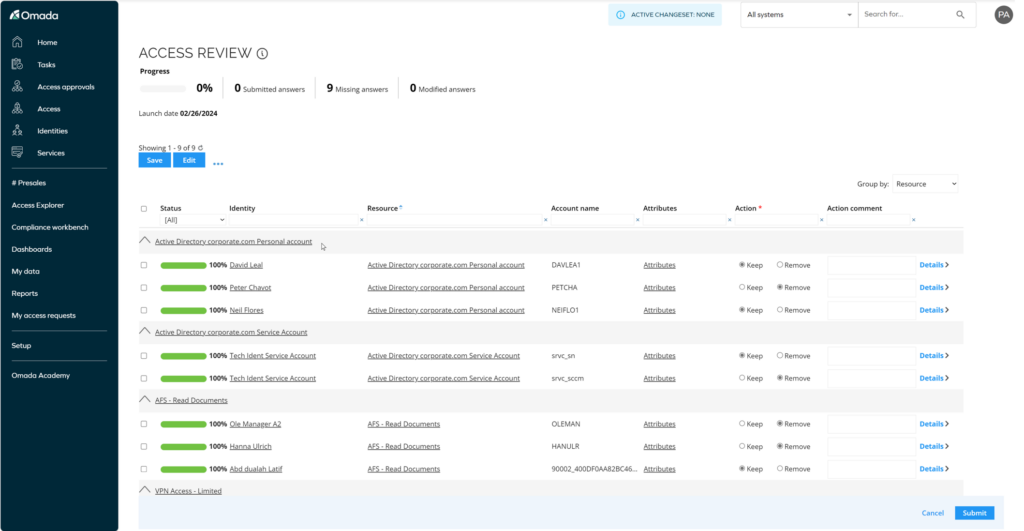
The Access Review feature is a predefined solution designed to make the execution of attestations (or recertifications)as convenient and efficient as possible.
Advantages
- Vendor specialized in IAM software for over 20 years
- Extensive range of standard features
- Fast and straightforward implementation
- Strong German-speaking team with direct access to the vendor
Disadvantages
- No online trial function like some competitors (though demos can be requested)
- Relatively limited customization options for highly specialized scenarios
Assessment
The strength of the Omada Identity Cloud is undoubtedly its ability to offer a solution that can best be described as feature-rich.
Those who choose the Omada Identity Manager receive software from a highly specialized company, offering a wide range of features that are often missing from other solutions—or that would otherwise require costly custom development.
Although the software originates from Denmark, customers can rely on a highly dedicated and capable German-speaking team that is open to incorporating specific wishes and requirements.
This level of closeness to the manufacturer is something you will likely miss with industry giants such as Microsoft or SAP.
If you’re looking for a solution that “just works” and can do without highly specialized SAP integration scenarios, the Omada Identity Cloud should, in our view, be among your top choices.
Option C: Okta
Okta is an independent provider specializing in identity and access management.
The platform is known for its flexibility and user-friendliness, offering a wide range of identity management functions, including Single Sign-On (SSO), Multi-Factor Authentication (MFA), and identity lifecycle management.
Okta places strong emphasis on integration with a wide variety of applications and platforms, making it a popular choice for organizations with heterogeneous IT landscapes that seek a seamless user experience across different applications.
From a technical and conceptual perspective, Okta represents a so-called Directory-as-a-Service (DaaS).
This means that, at its core, it is a directory service offered as a cloud-based service.
Directory services differ from identity management solutions in that they store and provide data about people and objects (e.g., network infrastructure) to third-party applications, without directly managing user accounts and permissions within those applications.
With this approach, Okta is in direct competition with Microsoft Active Directory (AD) and Entra.
Genau wie bei Microsoft Entra sind hier jedoch die Übergänge von einer DaaS-Lösung zum Identity-Management fließend und es können auch Provisionierungsszenarien konfiguriert werden. Okta besticht dabei durch eine, zumindest von uns wahrgenommene, höhere Flexibilität als bei Konkurrenzprodukten. Dies wird vor allem bei der Workflow-Funktionalität deutlich.
Okta’s pricing structure is highly individualized, which makes it appear fair and transparent.
It is based on the specific products a customer selects and the number of users who will be using those products.
The available products include Single Sign-On, Multi-Factor Authentication, Universal Directory, Lifecycle Management, API Access Management, and more.
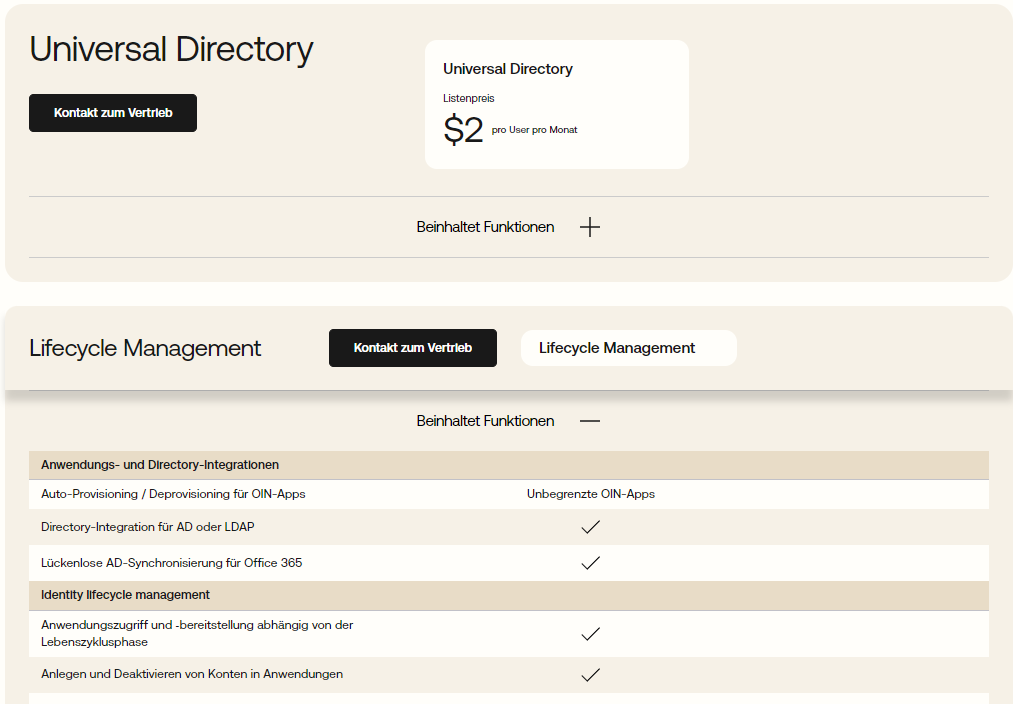
Each of these products has its own price per user per month.
In addition, there is a minimum annual contract.
For enterprise customers with a large number of users, volume discounts are available.
It is important to note that actual prices may vary, and it is best to contact Okta directly for the most accurate and up-to-date pricing information.
Advantages
- High degree of customizability for a cloud solution
- Strong global presence
- Considered user-friendly, lightweight, and quick to implement
- Highly individualized pricing model
Disadvantages
- On-premise infrastructure (e.g., Windows domain controllers) still requires classic Active Directory
- The core structure of Okta, as with most directory services, is group-based—there is no distinction between groups and roles
- Not primarily focused on the SAP-centric DACH market, resulting in limited SAP integration scenarios
Assessment
Okta is rated a “Leader” for Identity and Access Management solutions by Gartner, and likely not without reason.
With reportedly over 18,000 customers, Okta appears to be the most widely adopted IAM solution behind the Microsoft-dominated market, according to our research.
When using Okta, SAP integration scenarios should generally remain within the standard scope.
The availability of Okta experts in the German-speaking region also tends to be lower compared to other competitors.
Moreover, it is important to note that Microsoft-based on-premise infrastructures will still need to be managed via classic Active Directory.
However, if your company aims to become less dependent on Microsoft’s quasi-monopolistic market position, Okta is the right choice.
Its advantages lie particularly in being a highly adaptable, easy-to-implement, and industry-focused solution that can integrate nearly your entire infrastructure.
Option D: IBM Security Verify
As the fourth option, the solution from software giant IBM fits seamlessly into the world of cloud-based IAM solutions.
Since we have had fewer touchpoints with this product, this section will be somewhat shorter.
IBM Security Verify is the result of continuous development and refinement of IBM’s security solutions.
Before its introduction, the product was known as IBM Cloud Identity.
Many industry veterans will also remember the IBM Tivoli Identity Manager, which, in our assessment, was technically superior to SAP IDM in its time.
In the cloud era, however, the cards are being reshuffled, and IBM presents a solution that appears highly intuitive and familiar at first glance.
Among its features are SAML- and OIDC-based Single Sign-On, a “digital workspace” that — similar to a Citrix launcher — simplifies access to all authorized applications, adaptive access control powered by artificial intelligence, and industry-standard identity governance functions.
A look into the identity provider configurations shows that with IBM Security Verify, all common B2C authentication scenarios can be covered.
For example, implementing a LinkedIn-based login for your application can be accomplished in just a few clicks using a wizard.
On the other hand, as SAP-focused testers of the solution, we found only a preconfigured integration package for the classic SAP NetWeaver.
We found the Policy Editor to be well designed and neatly organized.
Here, security settings for groups of applications can be configured and audited easily and clearly, all within a clean and intuitive interface.
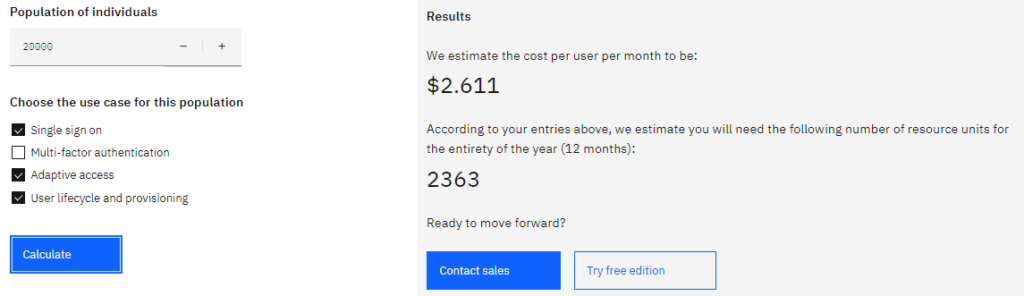
The pricing structure can be viewed and calculated exemplarily on the IBM Security Verify website.
As with other cloud solutions, the pricing primarily depends on which features are selected and how many identitiesare ultimately to be managed.
Assessment
Based on our initial demonstration, our impression is that IBM Security Verify is another well-structured DaaS solution equipped with the typical IAM features one would expect.
Whether the extensibility of the solution is as flexible as it once was with IBM Tivoli, however, cannot be assessed at this stage.
Given the relatively high recognition of IBM’s predecessor solutions in the German-speaking market, IBM Security Verify certainly deserves a mention.
Summary
Cloud computing is the talk of the town, and market competition continues to grow.
Even on-premise heavyweights such as Quest (more on One Identity in Part 4) are now positioning themselves with cloud-based versions of their successful products.
As a result, conducting a comprehensive evaluation of all available options is nearly impossible, and the final decisionfor or against a particular product often depends on how well it is positioned and marketed within the industry.
For SAP customers, we believe that the partnership between Microsoft and SAP will continue to dominate the market.
As a result, customers receive an infrastructure composed of products they would likely be using anyway—even when adopting a third-party IAM solution.
This helps streamline the architecture and thus provides strategic advantages.
However, whether this combined solution will be offered with the same focus and quality as that of a specialized vendor like Omada remains to be seen.
The lack of active support for SAP IDM in recent years may still leave a bitter aftertaste for some customers and could motivate them to look elsewhere in the market.
Next Part 4: On-Premise Solutions (e.g. One Identity)
Über den Autor

Hendrik Winkler is a partner at consiness and the lead architect for Identity and Access Management solutions. He draws on extensive expertise in SAP ABAP, GRC, cloud technologies, and SAP Identity Management. With more than ten years of experience in the IT industry, he has specialized in the development and implementation of complex IAM systems, always keeping a close eye on security, usability, and compliance.

