In the final part of this article series, we take a closer look at on-premise solutions.
Although the general trend clearly points toward cloud services, traditional solutions remain widely used within the SAP ecosystem.
The boundaries, however, are fluid — alongside the two solutions presented in this article, there are also on-premise variants of products such as Omada and IBM Security Verify (introduced in Part 3).
Conversely, One Identity has long since moved beyond the purely classical approach of installing software exclusively on in-house servers.
As this series hopefully illustrates, companies today are truly spoiled for choice.
Each solution discussed has its strengths and weaknesses, and has thus carved out its own niche in the market.
Please also note that the assessments provided here are not final and do not replace individual consulting.
For the product selection process, consiness offers a predefined evaluation matrix, which will be discussed at the end of this article.
Overview of the Series
- Part 1: The End of an Era – The Future After SAP IDM
- Part 2: SAP – Cloud Identity Services, GRC Edition for SAP HANA
- Part 3: Cloud Services
- Part 4: On-Premise Solutions – e.g. One Identity, SIVIS
Structure of This Article
- Option A: SIVIS
- Option B: One Identity by Quest
- Our Offer: The consiness Product Evaluation
Option A: SIVIS
SIVIS is a product that will immediately appeal to experienced administrators in identity and authorization management.
Developed by the Karlsruhe-based company of the same name, it is proudly “made in Germany.”
From our perspective, this represents a significant advantage, as the challenges of SAP-centric environments are particularly well understood within the DACH region.
It therefore comes as no surprise that SIVIS is an ABAP-based solution, offering an enhanced structure built upon classic SU01 user accounts and PFCG roles.
This positions SIVIS more or less in direct competition with SAP’s own GRC product line.
The feature set of SIVIS has clearly evolved from the day-to-day requirements of identity and access management in complex SAP landscapes.
Accordingly, SIVIS is delivered with its own risk analysis engine for object-level evaluation of SAP authorizations.
It can also fully replace SAP’s widely used Privileged Access Management solution (SAP GRC Firefighter), eliminating in most cases the need for third-party integration.
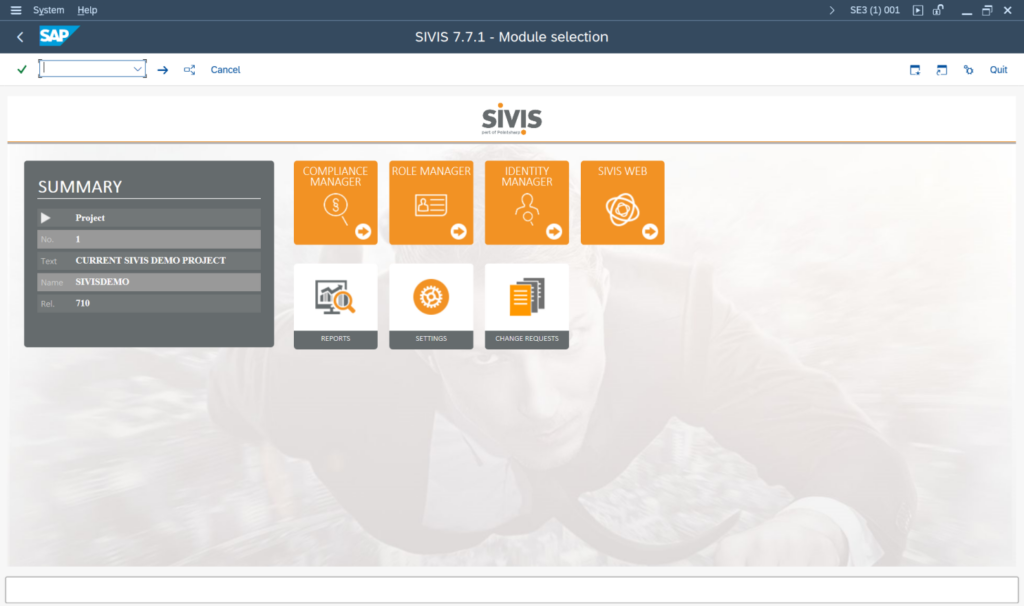
The aging Dynpro interfaces of ABAP are enhanced in SIVIS with a visually appealing, modern UI.
In the following example, a role assignment is shown that is based on workplace roles and can immediately flag potential issues using the integrated risk engine.
These workplace roles are not limited to SAP ABAP-based authorizations — they can be integrated with virtually any application through over 4,000 available connectors.
This includes classic integrations such as SAP BI, HCM, Active Directory, and various cloud applications.
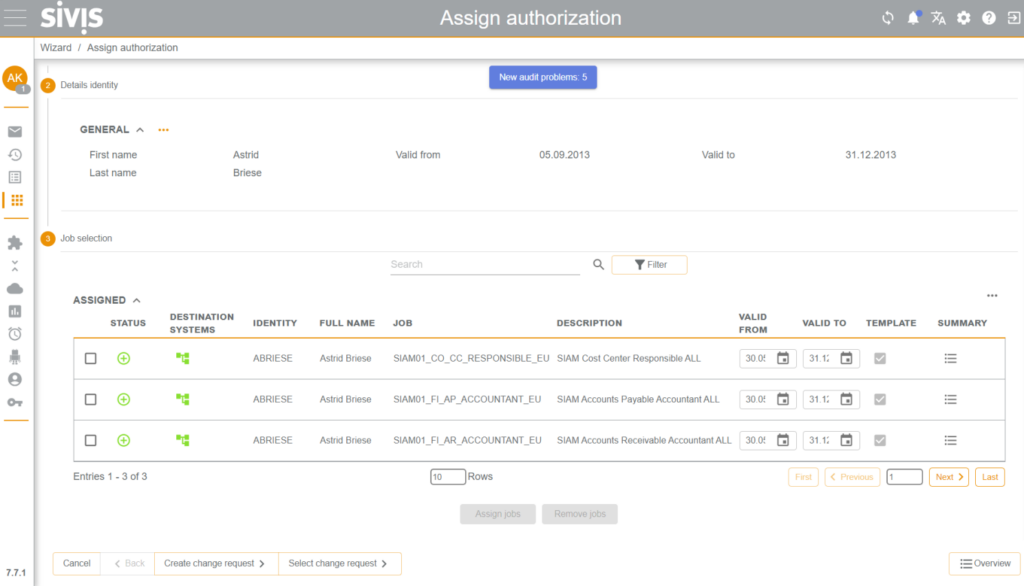
A particularly positive aspect to highlight is that the rule sets for critical authorizations and segregation-of-duties conflicts are presented not only from a technical perspective, but also in a business-oriented and detailed manner.
This makes the solution suitable for business departments as well, especially for those acting in the role of risk owners.
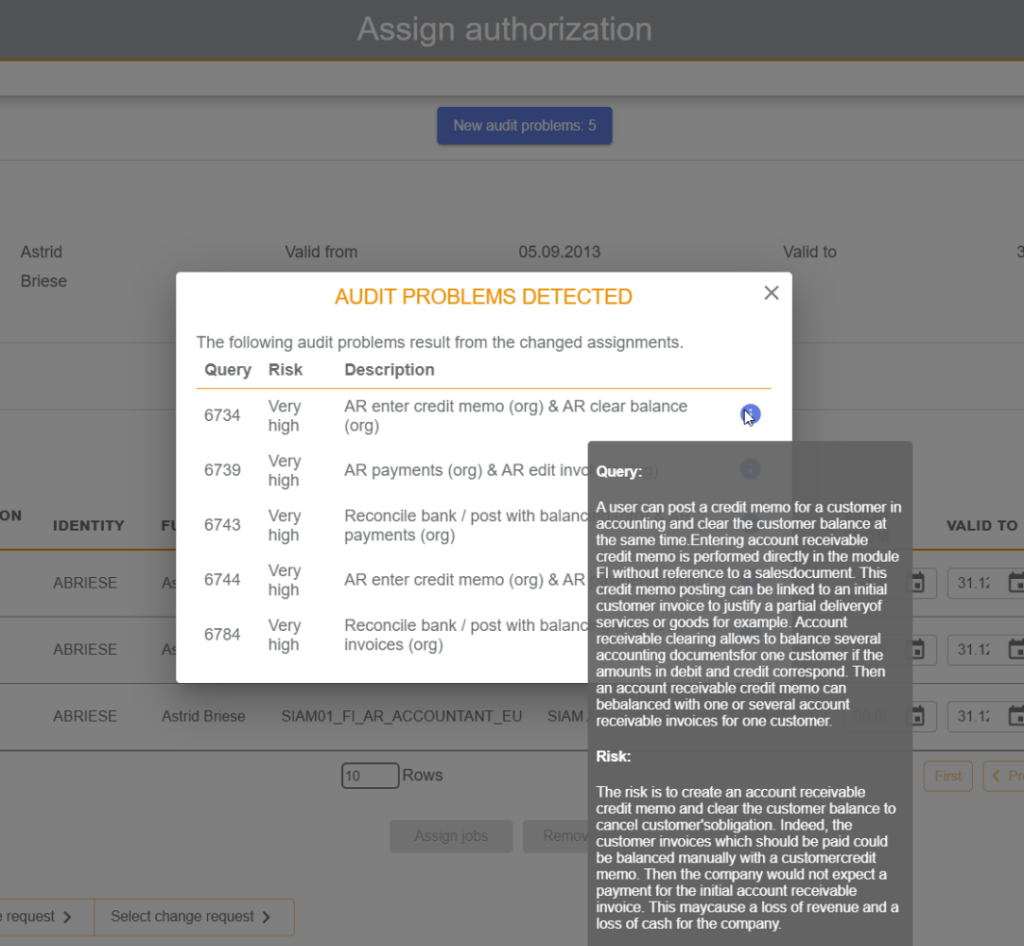
SIVIS is generally offered in four different editions, which vary in terms of functionality and connectivity.
The price of the solution is determined primarily by the selected feature set and the number of managed identities.
Although no specific pricing information is provided on the website, it can be assumed that SIVIS is priced below a comparable SAP solution.
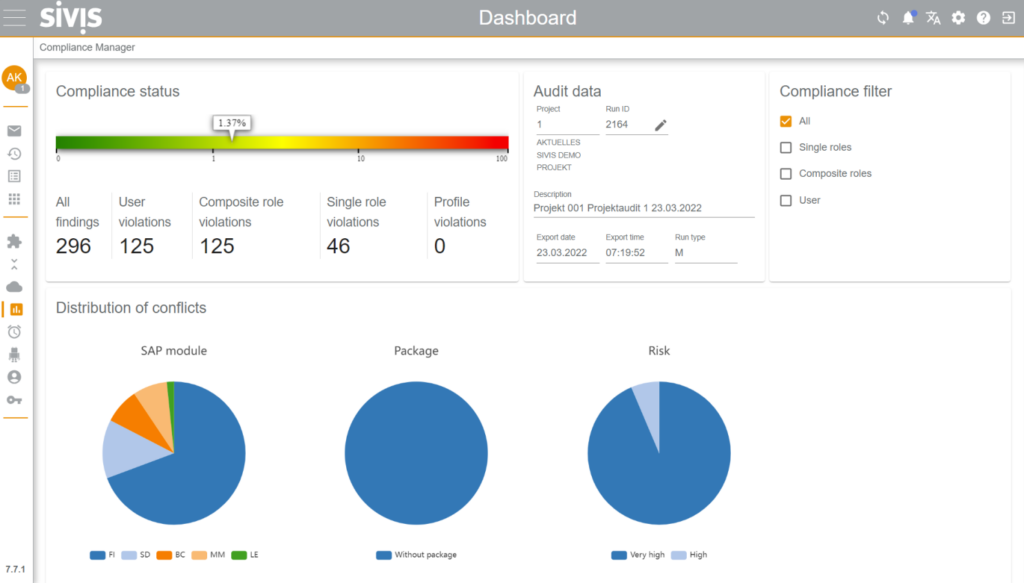
Finally, let’s take a look at the Compliance Manager dashboard, which is designed to clearly and management-friendly display the status of audit-relevant authorizations.
For authorization managers, this dashboard also serves as the primary point of entry for resolving or mitigating issues within the authorization concept.
Advantages
- SAP-focused solution from a highly specialized IAM vendor
- Supports both Microsoft and SAP platforms
- Close customer relationships with direct access to the manufacturer
- More attractive pricing model compared to SAP’s own solutions
- Integrated risk analysis engine capable of evaluating down to the SAP ABAP object level
- Built-in Privileged Access Management (PAM) solution
Disadvantages
- No Fiori-based interfaces for SAP
- Relatively small vendor compared to larger competitors
Assessment
We first became aware of SIVIS through a project with one of our partners at a major enterprise customer.
During a demonstration, we were able to evaluate the solution against some of the very specific requirements of one of our existing IDM clients.
Among all the options presented in this article series, none achieved such a high match rate and level of “out-of-the-box” support.
While many other solutions rely on third-party integrations for aspects like extensibility, PAM, authorization risk analysis, and specialized SAP provisioning scenarios, SIVIS can address all of these requirements natively.
Combined with its straightforward and goal-oriented architecture, it’s no surprise that customers choose SIVIS for the long term.
We can therefore give a clear recommendation for highly complex, SAP-centric architectures.
Right after logging in, users immediately get a sense of what kind of solution they’re dealing with: there are five main applications that can be accessed directly — the Manager, Designer, Synchronization Editor, Object Browser, and Job Queue Info.
The technology stack is based on .NET, providing virtually unlimited possibilities for customization and custom development.
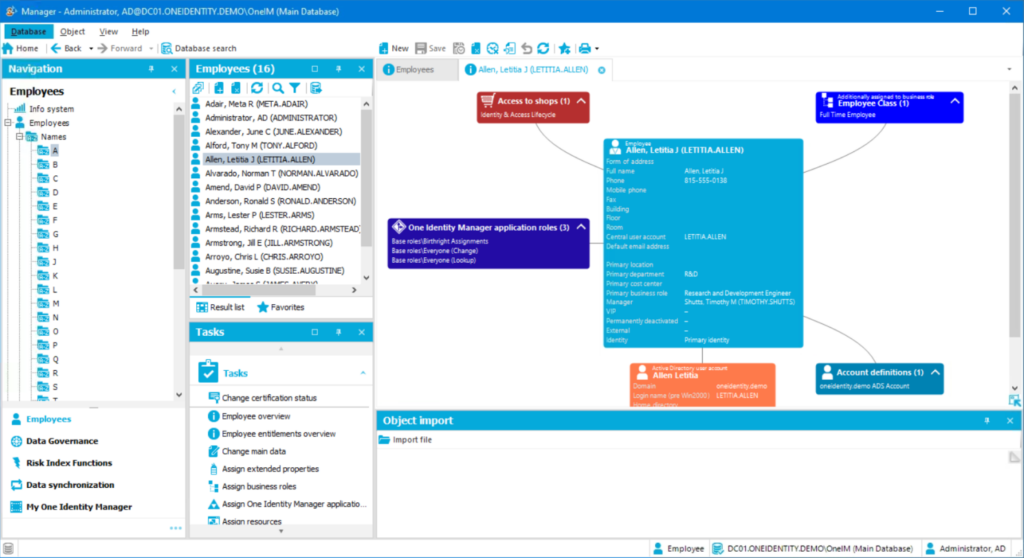
We consider the interfaces of the classic edition to be somewhat dated, yet still highly functional.
In the Manager, users can look up individuals much like in a telephone directory and receive a graphical overview of identity data, access rights, and permissions.
Key functions, such as assigning new privileges, are just one click away.
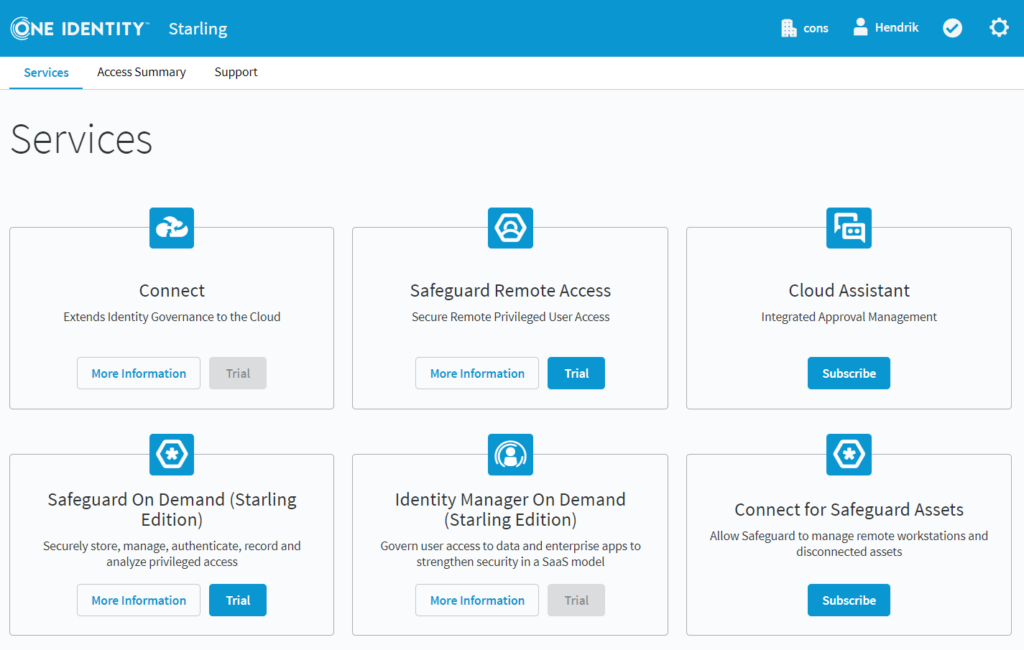
A look at One Identity Starling reveals that service- and cloud-based identity services are being rolled out in a much more contemporary design.
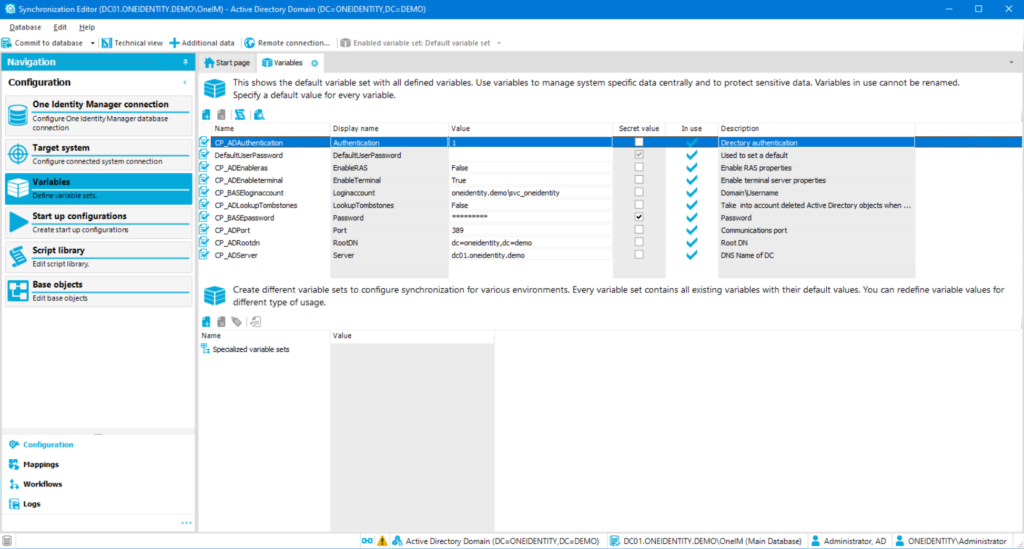
To provide a further impression of the customization capabilities, we’ll now showcase the options for maintaining scripts, connectors, and synchronization scenarios.
The script editor is integrated into the system with a graphical interface, allowing interfaces and relationships to be visualized directly.
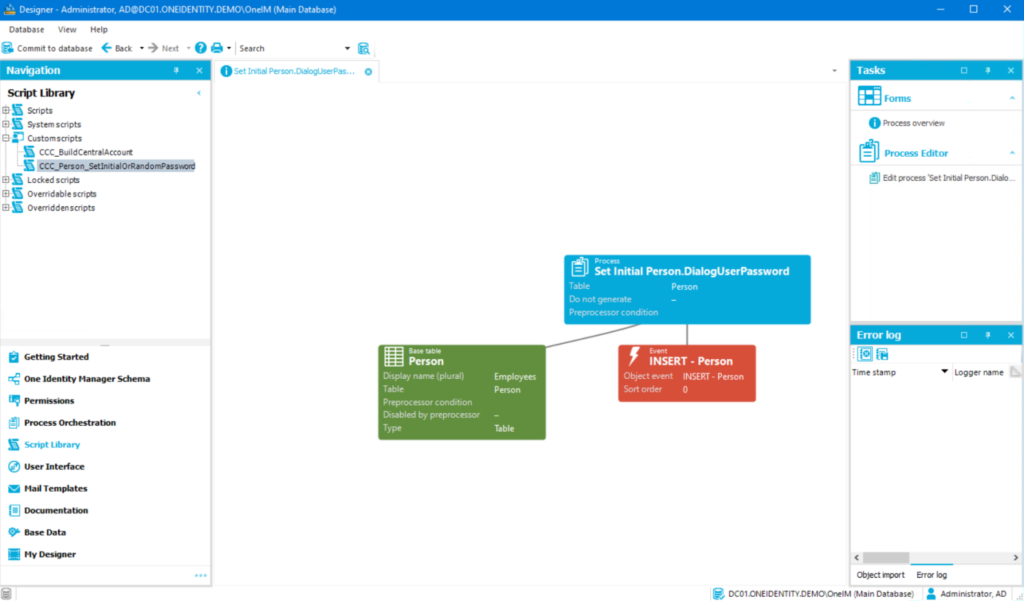
From our perspective, one of the major advantages of SAP software (and SAP IDM in particular) has always been its ability to accommodate highly complex scenarios and customer-specific requirements through customization.
Without judging whether a return to standardized processes might sometimes be the better option, One Identity should ensure that no requirements remain unsolvable due to technical limitations.
To get familiar with the world of One Identity, the One Identity University is prominently featured.
Depending on the required profile, training courses of varying scope and technical depth can be booked.
For service providers, onboarding can easily involve a full month of training.
This competitive advantage—along with the distinctive “moat” created by certified One Identity specialists—will likely feel familiar to seasoned SAP consultants.
When it comes to pricing, Quest unfortunately does not provide public information.
However, based on experience from our network, pricing appears to be roughly comparable to SAP licensing levels, though this can vary significantly between customers.
Advantages
- Established market-leading solution
- Maximum flexibility and complexity, strongly reminiscent of SAP IDM
- Cloud deployment also possible
- Extensive documentation and a clear training path through the One Identity University
Disadvantages
- Complex architecture
- Comprehensive training required for administrators and developers
- SAP-specific scenarios such as PAM and risk analysis require integration with SAP GRC
Assessment
As mentioned in the introduction, One Identity offers countless possibilities for building a tailor-made IAM solution— which can be either a blessing or a curse for potential customers.
Often, it’s only after implementation that companies realize their unique requirements and details.
With One Identity, virtually any imaginable scenario can be realized using built-in tools.
We therefore see One Identity as the solution that most closely resembles SAP Identity Management, offering similar flexibility.
However, the key differences lie in the fact that One Identity provides many more out-of-the-box features, boasts a larger customer base, and has a much longer history in the IAM market.
Moreover, Quest continues to innovate, now offering the solution as a cloud service as well.
From our perspective, it’s easy to see why One Identity is the market leader.
The only drawbacks are its high complexity and the fact that SAP integration scenarios have never been a primary focus for this internationally operating company.
Our Offer: The consiness Product Evaluation
consiness offers a specialized product evaluation for Identity and Access Governance (IAG) solutions, tailored to the individual circumstances of each client.
We apply a structured methodology to systematically analyze the available options and identify the best-fit solutionfor your organization.

Scoring:
Weighted evaluation of solutions based on their product features and framework conditions.
Cost Overview:
Rough calculation of operational and investment costs for a given solution over a 10-year period.
Roadmap:
A model project plan outlining the implementation timeline for the new solution.
Decision:
Comprehensive documentation of a justifiable and transparent decision for presentation to stakeholders.
The methodology presented supports organizations in making well-informed decisions — whether during the initial selection of an IGA solution or when reviewing existing choices.
In this way, we ensure that the selected solutions optimally meet the defined requirements and are future-proof.
A more detailed insight into the consiness Product Evaluation will be published soon on LinkedIn.
Summary
With this article, we conclude our four-part series, in which we presented a variety of available options.
Each of these solutions occupies its own niche and justification, addressing different requirements and preferences.
Despite the detailed overview provided, a precise product evaluation tailored to individual customer needs cannot be replaced.
It remains essential to carefully analyze your specific requirements and expectations in order to select the optimal solution for your organization.
Of course, there are many other solutions that did not make it into this series — we plan to cover additional ones in future articles.
In conclusion, we hope that we have kept your interest and provided a clear and comprehensive overview of the diverse world of IGA solutions — from the perspective of an SAP consulting firm.
about the auto

Hendrik Winkler is a partner at consiness and the lead architect for Identity and Access Management solutions. He draws on extensive expertise in SAP ABAP, GRC, cloud technologies, and SAP Identity Management. With more than ten years of experience in the IT industry, he has specialized in the development and implementation of complex IAM systems, always keeping a close eye on security, usability, and compliance.

